32+ network security diagram example
MD5 Message Digest Method 5 is a cryptographic hash algorithm used to generate a 128-bit digest from a string of any length. Encapsulating Security Payload ESP provides all encryption services in IPSec based on integrity for the payload and not for the IP header confidentiality.

Security Assessment Plan Template Inspirational 10 Security Plan Templates How To Plan Business Plan Template Free Business Proposal Template
Security in Network Layer.
. DES is a block cipher and encrypts data in blocks of size of 64 bits each which means 64 bits of plain text go as the input to DES which produces 64 bits of ciphertext. In the example diagram above you can see a simple 32 camera Imperial setup. Network security is a computer networking system policy to assure the security of its organizations assets software and hardware resources.
It is a feature of almost every. Creating the mind map. A static IP address is a 32 bit number assigned to a computer as an address on the internet.
In LAN1 we have a connection going to the main network. Up to 24 cash back Software Features. State of the art.
This number is in the form of a dotted quad and is typically provided by an internet service provider. This can either be directly to the network or. It represents the digests as 32 digit.
The term network security. Unlike broadcast television this system has only local signal. Support for network design installation and commissioning and training for Simon employees.
Redundant Industrial Ethernet rings with 32 SCALANCE XR524 switches and connection of. Any scheme that is developed for providing network security needs to be implemented at some layer in protocol stack as depicted in the diagram below. CISA has published an infographic to emphasize the importance of implementing network segmentationa physical or virtual architectural approach that divides a network into.
The first step in the process of creating a network diagram is to create a mind map of all the systems anddevices in your network that you can. An IP Address is a 32-bit numeric address written as four numbers separated by periods For example. Visio is a diagraming tool that makes it easy and intuitive to create flowcharts diagrams org charts floor plans engineering designs and more by using modern templates with the familiar.
Closed-circuit television CCTV uses cameras and monitors to carry out video surveillance. An all-in-one network diagram makers which can make over 200 kinds of diagrams. The LAN uses IP addresses to route data to different destinations on the network.
A network diagram is a visual representation of a computer or telecommunications network. It shows the components that make up a network and how they interact including routers.

Field Notes How Olx Europe Fights Millions Of Bots With Aws Aws Architecture Blog
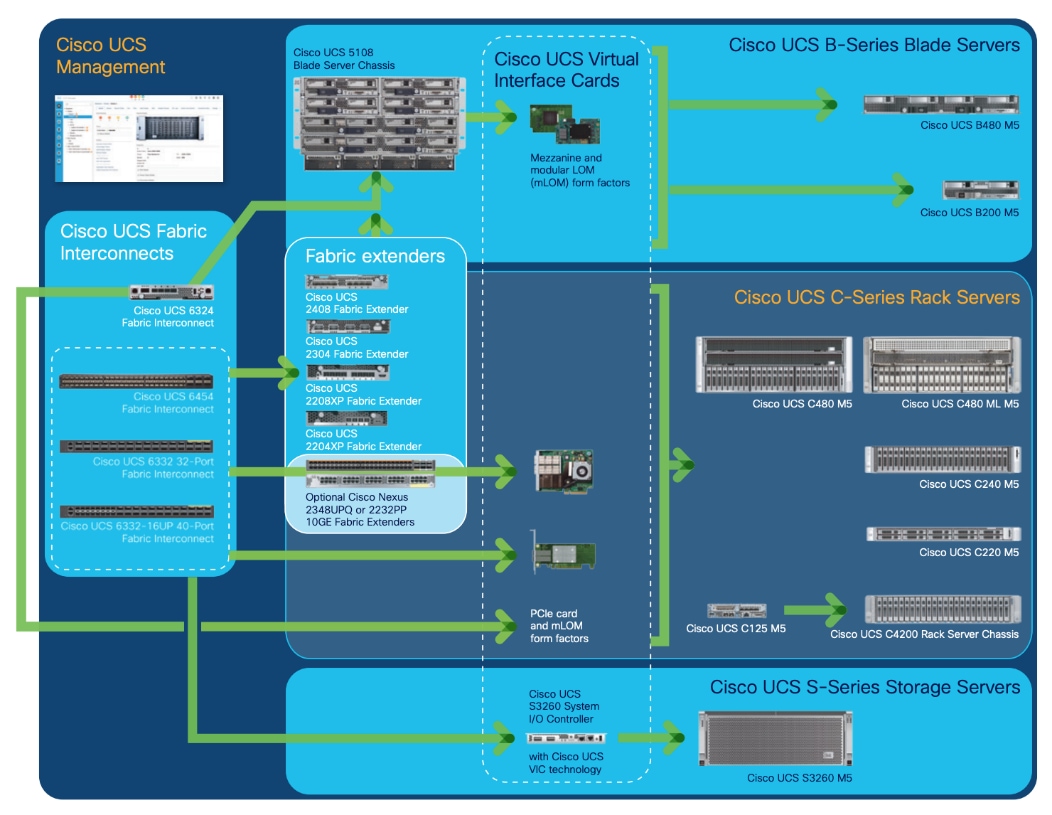
Cisco Data Intelligence Platform On Cisco Ucs C240 M5 With Cloudera Data Platform Private Cloud Experiences Cisco

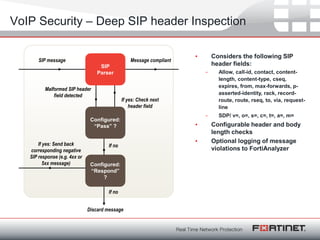
Plnog 5 Rainer Baeder Fortinet Overview Fortinet Voip Security
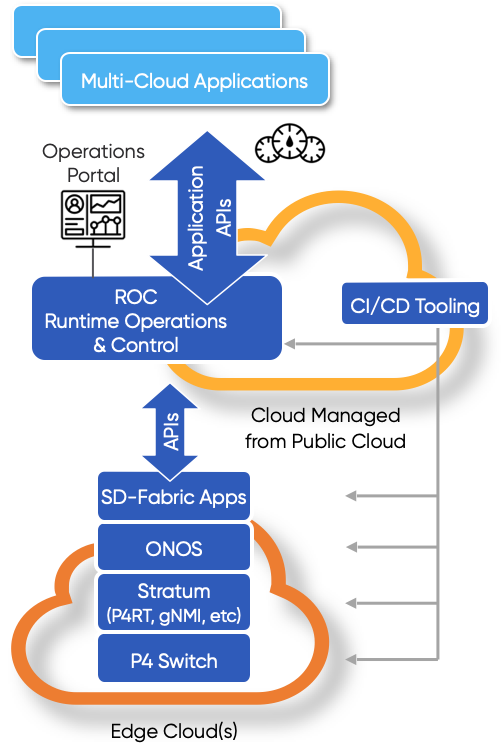
Onf Announces New Sd Fabric Project An Open Source Full Stack Programmable Network Fabric For Hybrid Cloud Edge Cloud 5g And Industrial Iot Open Networking Foundation

Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco
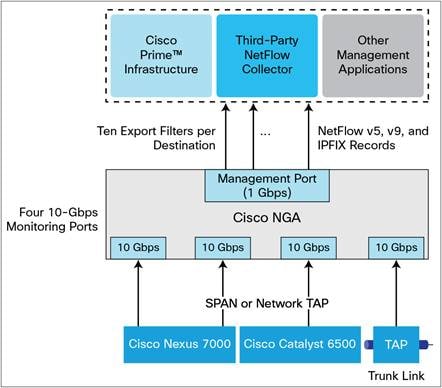
Cisco Netflow Generation Appliance 3340 Data Sheet Cisco

Cisco Data Intelligence Platform On Cisco Ucs M6 With Cloudera Data Platform Private Cloud Cisco

Guide To Subnet Mask Subnetting Ip Subnet Calculator

Guide To Subnet Mask Subnetting Ip Subnet Calculator
2

Guide To Subnet Mask Subnetting Ip Subnet Calculator
Plnog 5 Rainer Baeder Fortinet Overview Fortinet Voip Security

Pin On Drones

Interfacing Rfd900 Telemetry With 3drobotics Pixhawk Telemetry Drone Design Diy Drone

Guide To Subnet Mask Subnetting Ip Subnet Calculator

64 Channel 64 Pack 5mp Poe Nvr 4k Security Camera Gw Security
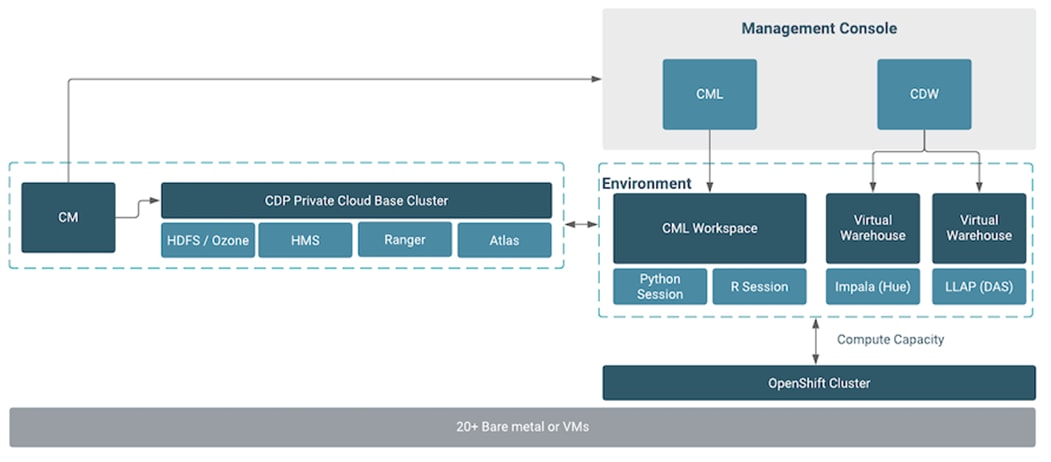
Cisco Data Intelligence Platform On Cisco Ucs C240 M5 With Cloudera Data Platform Private Cloud Experiences Cisco